- +91-9035052556
- Indiranagar, Benguluru, Karnataka 560038
- info@atosor.in
Today sophisticated attackers continue to circumvent perimeter defenses and target the data and applications at the heart of your business. Their goal is to attack the very systems and data that help you to create and keep customers, manage and create intellectual property, and maintain a positive cash flow.
At Atosor we have a proven approach to Application security and we provide the best detection and the greatest coverage by identifying malicious content, communications, and behavior across every stage of the attack sequence.

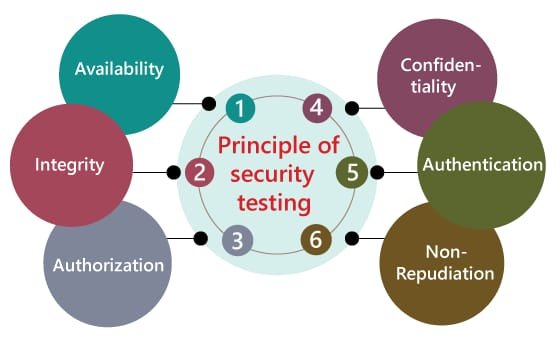
Application Security Testing Service is meant to discover security vulnerabilities in your web site from an attacker’s perspective. At Atosor, Our inhouse team of web security experts will analyze your web site with web security scanners, custom security tools, and comprehensive manual inspection to identify each potential point of intrusion into your web site.


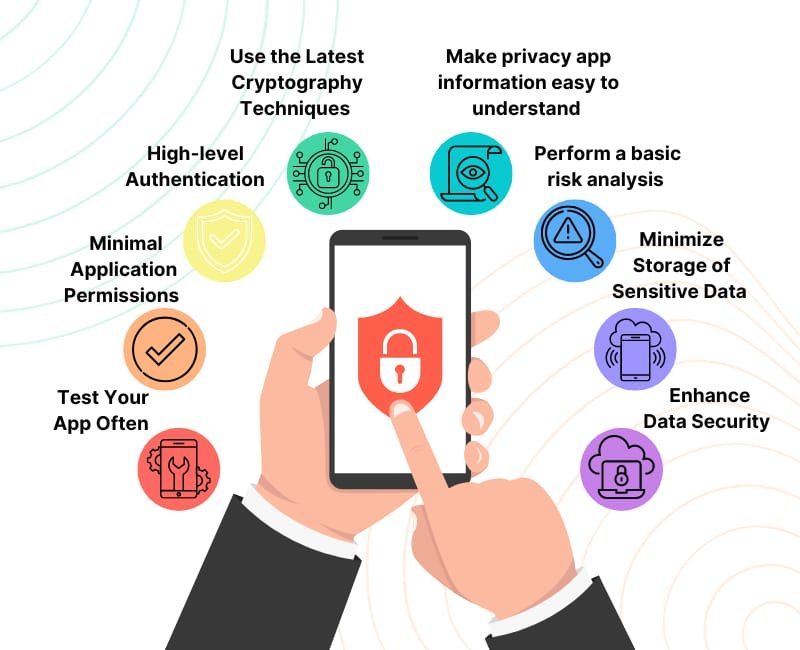
Atosor Mobile App Security Testing service provides a detailed security analysis of your mobile app.Gartner CIO survey believes mobile technology will remain a disruptive force for the next 10 years.90% of the top mobile apps have access to local files that can contain sensitive customer data, corporate intellectual property, and personally identifiable information.mobi Atosor follows these steps to reduce the mobile risk. We follow this procedure for mobile app testing, Submit web interface to our cloud-based platform.Inform policy development process, which helps enterprises getting started on their mobile application security programs.Risk quantification would be done for both malicious and safe applications using advanced machine learning technology. Integration of Mobile Device Management solution with API.

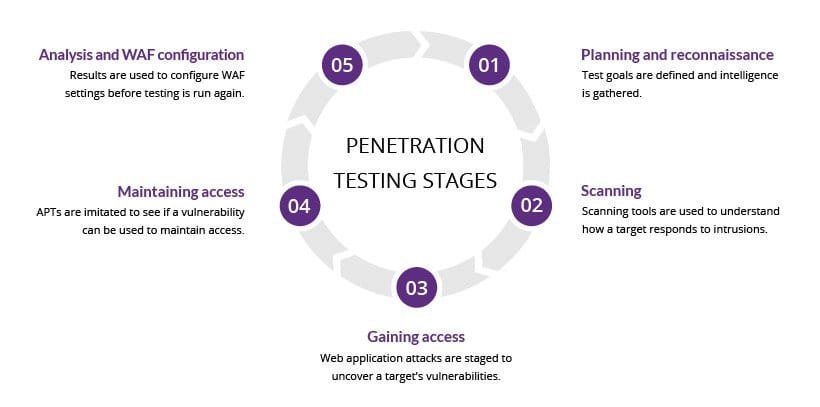
At Atosor we help you identify security vulnerabilities in your system before they explode. Atosor discovers vulnerabilities before hackers do,audits the effectiveness of implemented security measures,prevents from data loss and also has the ability to manage IT security risks and plan for the future.

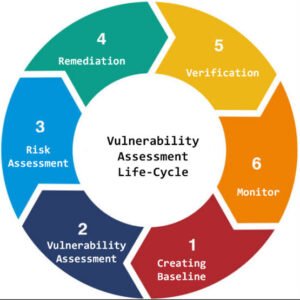
Atosor Secure is a vulnerability assessment service which is designed to identify critical flaws in your network that an attacker could exploit. Today we have hundreds of applications and systems across your environment with access to the Internet, maintaining and updating system and applications to eliminate vulnerabilities is a necessity.
At Atosor we follow a methodology which is frequent and multi-phase process by which we assess the security of your network and systems. We use commercial and publicly available tools, as well as custom scripts and applications which we have developed.

If you’re concerned that your web application has security issues, and you’re looking for an independent review that will not just take your money and declare everything is fine without even considering the obvious don’t worry, Atosor Source Code Security Analysis is a perfect way to have your web application source checked for vulnerabilities and design flaws that could jeopardize your business. Atosor also takes care of web application security analysis service.
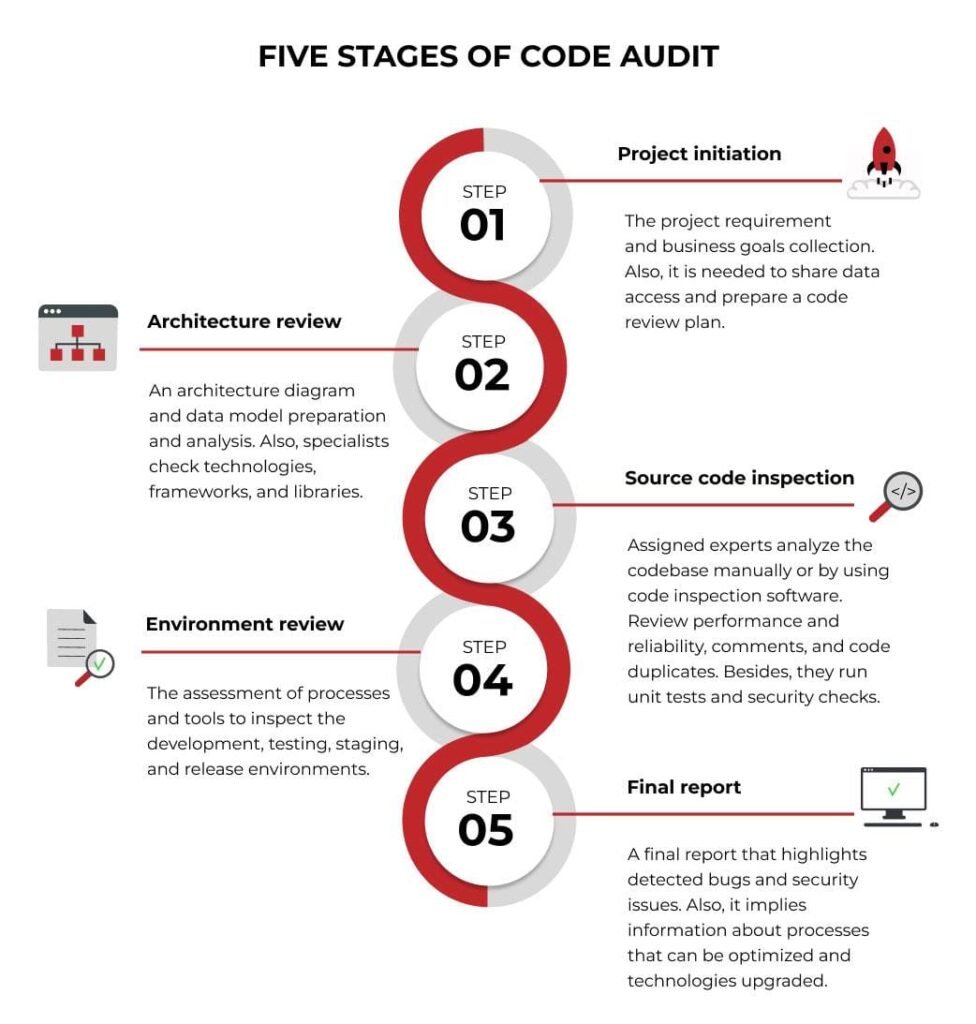

If you’re concerned that your web application has security issues, and you’re looking for an independent review that will not just take your money and declare everything is fine without even considering the obvious don’t worry, Siri’s Source Code Security Analysis is a perfect way to have your web application source checked for vulnerabilities and design flaws that could jeopardize your business. Siri also takes care of web application security analysis service.
As a app web crawler expert, We will help to organize.

An IT firm or MSP who keeps your IT running smoothly at all times is like a plumber who fixes your pipes that’s what they are supposed to do. Many IT firms struggle.